I would like to start this post out by saying that this post is BY NO MEANS a fix all solution. Every malware (viruses too, but I’ll simply referring to them both as malware) is different. As the malware-software-writing turds get better at creating their malware they are constantly changing how they infect a system. Most of them are pretty easy to remove, but, others can be a real pain depending on the types of defenses the malware has in place. Also, understand that you use this information at your own risk. I am not responsible for any harm you may cause your system. It is important that you understand what you are doing BEFORE you do it. This post is written for people that should have good solid experience with computers, if this is not you, you may want to find someone to help you out.
In order to successfully infect a system, malware has to be executed somehow. This can be done by tricking a user into running an infected program or it can even be done without user intervention by exploiting security holes found in the user’s system. When the computer is turned off the OS, all the applications and any existing viruses are killed and no longer running. Their processes are terminated. So, for malware to be effective the malware needs to be able to survive a reboot. The malware does this is by finding a way to tell the operating system to launch the malware on the next reboot. This way the malware can always be sure it is running. The areas below are places I find that malware developers target the most because they help meet this very need.
For quick reference for those that bookmark this page, here they are. They are explained further below.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run Startup Folders [Current User & All Users] HKEY_CLASSES_ROOT\.exe\PersistentHandler HKEY_CLASSES_ROOT\exefile\shell\open\command
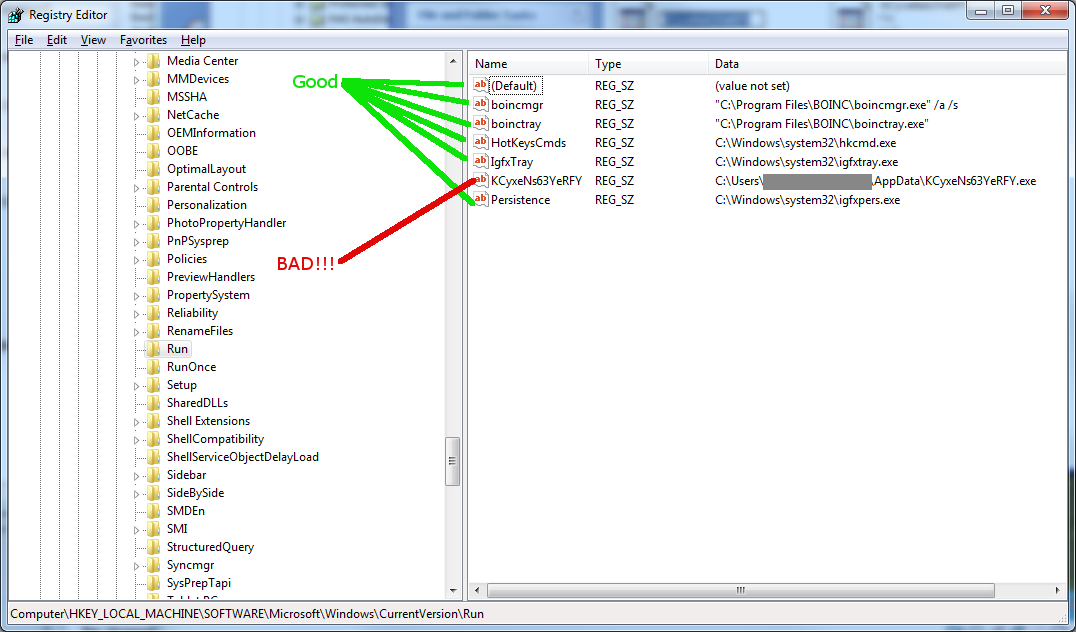
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run This is usually the first place I check. HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run is a registry key used to tell Windows which programs to run when a specific user logs into the computer. So when a user logs into the computer anything under this registry key will be executed. It is a HIGHLY targeted area for malware developers to attack! Since it is located under HKEY_CURRENT_USER the user will have full access to read & write any changes here. So for malware developers it’s the proverbial low hanging fruit because it’s easy to write anything you want under this key.
Since this registry key is SPECIFIC TO THE USER it will only affect the user currently logged into the computer. So if ALL users are seeing the same infection on this computer, it is not likely located here (You may want to check the next registry key located under HKEY_LOCAL_MACHINE). What you are looking for here is anything that looks out of place. If you’re not familiar with the registry, most of it probably looks out of place! However, You should have a good feel of what you want running on your computer.
Some things to look for under this key would be .EXE files with random letters (ie. Hf&21fe~!.EXE). It’s uncommon for normal software developers to use names so cryptic, it makes their job harder. Malware, on the other hand, will often use random .EXE names in order to prevent detection by antivirus software as the malware .EXE could now be named anything. If you find one and you feel the .EXE is malicious, make note of the path, delete the registry value and delete (or at least rename) the .EXE.
Another thing to look for are entries that run programs stored in the user profile. In Windows XP this would be C:\Documents and Settings[USERNAME]... For Vista and Windows 7 it would be anything under C:\Users[USERNAME]. The user profile is writable by the user and therefore an easy target. Do the same as above, make note of the path, delete the registry value and then delete the .EXE.
One more thing to for look for here are programs called with “Rundll32”. Rundll32.exe itself is not malware (though some malware may disguise itself as rundll32.exe). It’s a legitimate .EXE used by Windows. If rundll32.exe is located in the System32 directory, it’s probably ok. What you should look for is the file that is listed directly after rundll32.exe (ie. “rundll32.exe ‘C:\Documents and Settings[username]\Application Data\blahblahblah”). The blahblahblah is the file I would be concerned about. Keep in mind that legitimate programs can also use rundll32.exe, so before you delete anything be sure you know what you are deleting.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run This registry key is pretty much the same as the HKEY_CURRENT_USER key above with the main difference being that it is SYSTEM WIDE. The entries under this key will be executed by any user that signs on to the computer. It’s not targeted as much as HKEY_CURRENT_USER because you need Administrative privileges to write changes here. However, some malware will still try to write here because if they are able to the benefit is that they can be sure their malware runs anytime ANYONE signs on to the computer, not just the person that caused the initial infection.
You are looking for the same types of entries here as the HKEY_CURRENT_USER key above.
Startup Folders [Current User & All Users] The startup folder dates WAY back to Windows 3.1 (probably even earlier) and it is still used to this day. It’s purpose is very similar to the Run keys above, it runs programs when a user signs in. The difference is that this is a folder, not a registry key.
The default startup folder locations for all users. Anything located in these folders will be executed when ANY user signs on to the computer.
Windows XP - "C:\Documents and Settings\All Users\Start Menu\Programs\Startup" Vista / 7 - "C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Startup"
The default startup folder locations for a specific user. This applies only to the specific user and will not affect others that sign on to the system.
Windows XP - "C:\Documents and Settings\[USER NAME]\Start Menu\Programs\Startup" Vista / 7 - "C:\Users\[USER NAME]\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup"
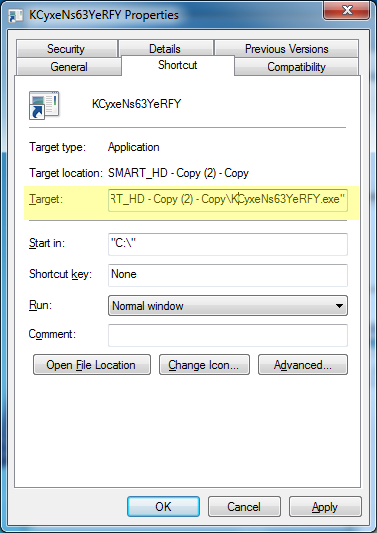
In these folders we are again looking for things that don’t belong or look suspicious. The same type of rules apply here as they do in the Run keys above (ie. random characters). Most of time, however, the items listed in these folder will be shortcuts (or links). So in order to be sure we find the executable culprit, we need to Right-Click on the suspected file and choose properties. On the Shortcut tab, it will give us the Target. The target should be the actual executable file that will run. Make a note of the path, delete the shortcut, and then rename or delete the executable.
File Association .EXE Hijacking These next two registry locations handle the file associations of .EXE files. Basically, A file association is how Windows knows what program to use to open a certain type of file. For instance when you click on a .XLS file, Windows knows to open Excel. If you click on a .PDF file, Windows will know to open Adobe Reader.
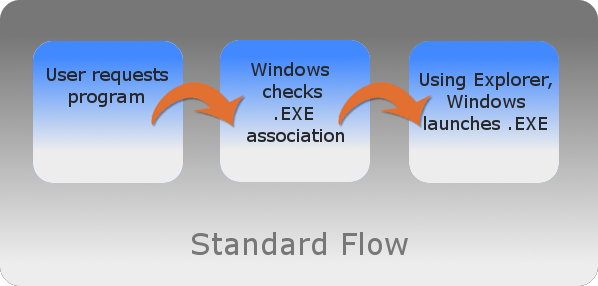
Windows also has file associations for .EXE files. In normal situations when a user clicks on an .EXE, Windows will check the assocation for .EXE files and then use Explorer to launch the requested .EXE. Everyone is happy.
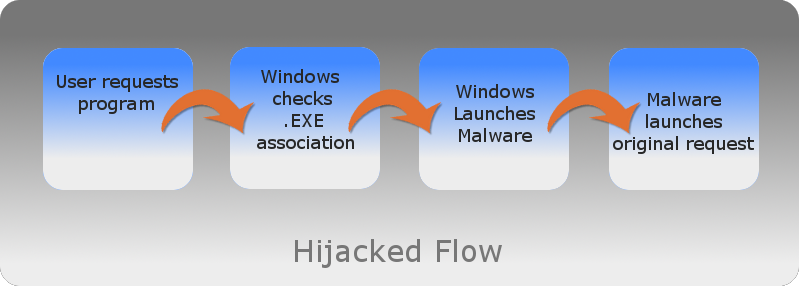
However, malware can hijack the association so that anytime an .EXE is run, the malware is run. Once the malware runs, it will usually run the originally intended .EXE and the user is none the wiser to what’s occurring in the background. The result is the malware runs.
To check that this isn’t happening you’ll want to check these registry keys:
HKEY_CLASSES_ROOT\.exe\PersistentHandler
(Default) value should equal: {098f2470-bae0-11cd-b579-08002b30bfeb}
HKEY_CLASSES_ROOT\exefile\shell\open\command
(Default) value should equal: "%1" %*
IsolatedCommand value should equal: "%1" %*
That covers the first places I check when troubleshoot malware problems. I hope that reading this article has taught you something and you may be able to approach your issue with a little more insight than before.
Again, please let me stress that this will not fix ALL the malware issues out there. If you’re still having problems getting it cleaned up be sure to ask your “computer guy” to give you a hand. If you do, be sure to buy him/her lunch or something. Most of us are really nice people and won’t make a big deal out of it but I can tell you that showing your appreciation with some food or GASP even a little money would stand out as it doesn’t happen that often. It would also be greatly appreciated! …Oh, and there’s always My Amazon Wishlist! :)