Google announced recently that they noticed some strange patterns of activity during some routine maintenance at one of their datacenters. The patterns were tied to malware infections that sent users through a custom Internet proxy which falsified search results. The pages listed in the results were usually that of other mal-intent in order to further infect a user’s computer.
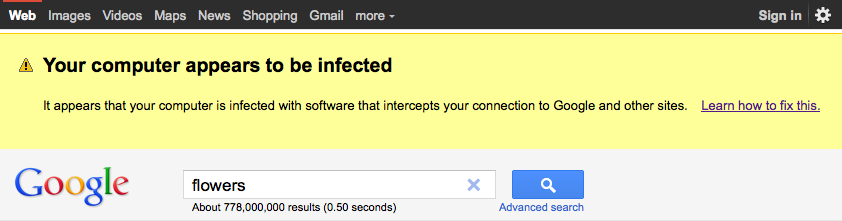
To combat this they are displaying a message on the Google home page for computers that are affected. It looks something like this.
I am assuming they are able to detect it by looking at the source of where the traffic is coming from. Since the malware they are targeting redirects through an Internet proxy, if the traffic comes from that proxy server the message will be displayed.
If you see the message above it is likely that the computer being used is infected and needs to be cleaned. There has been some concern generated from other admins that the scammers will now use the message above to mimic since it has the Google approval and has merit. Google considered this and wasn’t too concerned by it because the only way to show a falsified message is to be infected in the first place!
Just thought you may be interested if you get questions about this.